I remember downloading Android Studio back in 2013 to work on an Android project. But after playing around for an hour or two, I got frustrated. I had to delete Android Studio and go back to Eclipse. One reason why Eclipse was never successful with android because of patchy user interface for building Android applications, unfortunately that’s still the case in 2018.
Well, at least Google has made significant changes with Android Studio from 2015. It is almost compulsory to use Android Studio to build any new android applications. But there are few eclipse devotes like me who were still using eclipse to build android applications.
In this post, I will show how to migrate an android project from Eclipse to Android Studio. Warning: Even though the post looks very simple, it took me sizable efforts to figure out this migration. Hope it will be easier for readers.
Steps to migrate from Eclipse to Android Studio
- Download Android Studio from here. I had downloaded Android Studio version 3.3 RC2, but for it kept giving me syncing error when I imported the project. So I downgraded Android Studio version 3.2.1. Install Android Studio on your environment.
- On starting screen of Android Studio, you will see an option to import existing ADT project. Here you choose your eclipse based android project.
- Other option in this scenario, is to export android project from eclipse as gradle based project and it will also make life easier to import that project in Android Studio.
- Once you import the project in Android Studio, it will take some time to sync. In sync, Android Studio is basically creating gradle
buildfile for your project. Converting all your library jars into dependencies. Other task it will be doing is to merge all your AndroidManifest.xml files. If there are any errors, it will show those errors during sync. Easiest way to fixAndroidManifest.xmlerrors are to go to this screen:
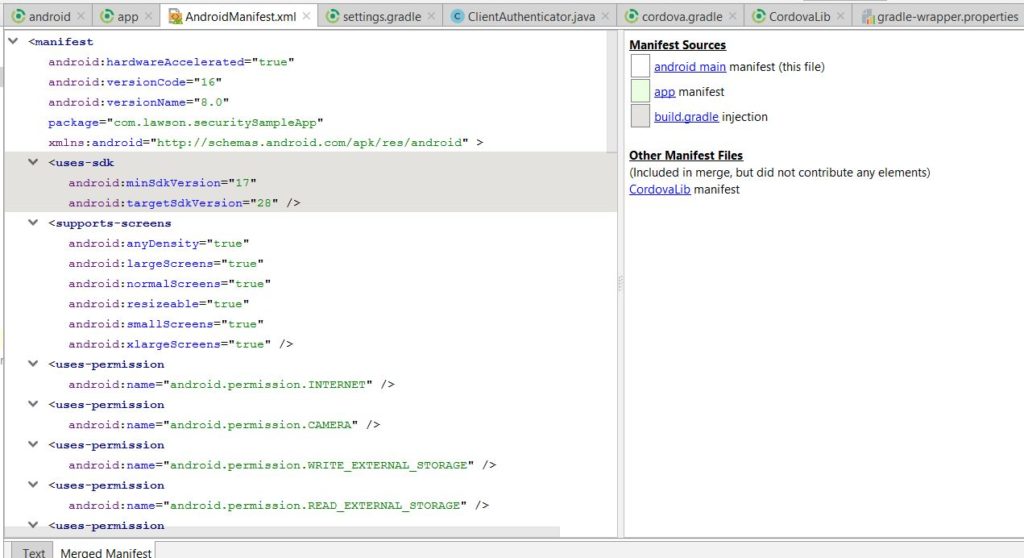
compile has been replaced by implementation project OR implementation files. Also to pull most of your dependencies, you will have to add google() as maven URL. minSdkVersion and targetSdkVersion should be moved to build file now and you can remove that from AndroidManifest.xml . Most of this should let you build your project successfully.
Conclusion
In this post, I showed how to migrate from eclipse to android studio for your android project. It is straight forward, but definitely depending on the project, you will run into few issues that you will have to resolve while building the project. Send me email or comment on this post if you have any questions.